Table of Contents
ToggleIntroduction
Cybercrime attacks have increased in recent years, emphasizing the need to understand hacking and cybercrimes to protect ourselves. Both businesses and individuals should familiarize themselves with the good and the bad types of hacking. This blog sheds light on ethical hacking, the key concepts related to ethical hacking, types of ethical hacking, and more.
Evolution of the Term Hacker
The emergence of hacktivism and cybercrime in the 1990s changed the way people look at hacking today. Initially, the term “hacker” was used to refer to skilled programmers who pushed the limits of technology to make it efficient. However, the rise of computers in the 1980s also brought to light increased illegal activities, like individuals breaking into computer systems and exploiting early computer networks.
Consequently, hacktivism emerged in the 1990s and was used to refer to actions where hackers attacked websites for financial gain or propaganda. When ethical hacking was formalized in the 2000s, the cybersecurity industry started hiring certified ethical hackers to find and fix security vulnerabilities, helping organizations protect their systems. This helped reclaim the term in a positive light within the tech community.

Don't miss out on your chance to work with the best
apply for top global job opportunities today!
What is Ethical Hacking?
Some experts bypass the security mechanisms of computer networks to target vulnerabilities and cause data breaches. On the other hand, some experts use their IT skills to help companies build their defense against cyberattacks. Ethical hacking is an approach where a certified ethical hacker will legally break into systems or applications to find weaknesses. Ethical hacking follows the same five-step hacking process (that a black hat hacker would use) to gain authorized access to an organization’s systems to check how good its strategies and networks are.
What do Ethical Hackers Do?
Identify Vulnerabilities
Ethical hackers conduct comprehensive reviews of an organization’s systems by thoroughly scanning and testing systems. The results are used to uncover security weaknesses that malicious hackers could exploit.
Penetration Testing
They simulate cyberattacks to evaluate the security of systems, networks, and applications, identifying potential entry points.
Security Audits
Companies hire certified ethical hackers to conduct comprehensive reviews of their security policies, procedures, and controls to ensure their effectiveness.
Risk Assessment
Ethical hackers evaluate the potential impact of identified vulnerabilities. Additionally, they recommend measures to reduce risks and enhance overall security.
Incident Response
Ethical hackers are called in after a security breach to investigate the incident. They determine the cause of the incident and develop strategies to prevent future attacks.
Training and Awareness
Companies also invite ethical hackers to educate employees and stakeholders about security best practices. The training sessions also teach how to recognize potential threats and foster a security-conscious culture.
Compliance
Ethical hackers make sure that organizations adhere to the relevant security standards and regulations, helping them avoid legal and financial penalties.
What Are The Five Phases of Ethical Hacking?
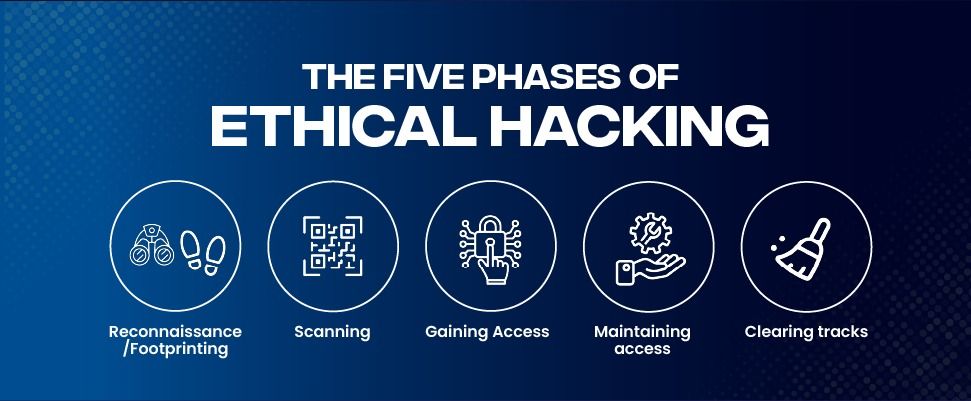
Reconnaissance
Also known as footprinting, reconnaissance is the first and most crucial step in which the hacker collects information about the target systems through footprinting, scanning, and enumeration. It can be active or passive. Active reconnaissance refers to interacting directly with the target systems. However, this may warn the target of the scans. Passive reconnaissance allows ethical hackers to collect data without direct contact with the target without being traced. Nmap, Whois, and Maltego are some popular tools used for reconnaissance. The common reconnaissance techniques in use are:
- Google Dorking
- Whois lookup
- Social engineering
- DNS enumeration
- Network scanning
Scanning
Once the hacker has adequate information about the target system, they scan it for open ports, services, and vulnerabilities. Scanning involves learning about the operating system (OS) and helps ethical hackers find potential entry points into the target system. Port scanning uses Nmap or Angry IP Scanner to find open ports or services. Vulnerability scanning uses Nessus to detect known weaknesses in systems and applications. Network mapping is a type of scanning where hackers use tools like SolarWinds to create a blueprint of network topology. The common techniques used for scanning are:
- Port scanning
- Vulnerability scanning
- Network mapping
- Banner grabbing
- Ping sweeps
Gaining Access
The third phase of ethical hacking involves using the identified weaknesses to gain unauthorized entry (within legal limits) into the target system. Ethical hackers use applications, operating systems, or network flaws to get access at different privilege levels. Hackers can get into the systems as users or administrators by using methods such as buffer overflows, SQL injection, and cross-site scripting (XSS). Tools such as Metasploit, SQLMap, and Hydra can be used for gaining access. Here are the techniques used for gaining access:
- Password cracking
- Exploring vulnerabilities
- Privilege escalation
- Session hijacking
- Man-in-the-Middle (MITM) attacks
Maintaining Access
Once the ethical hacker gets inside a system, they must stay there. In ethical hacking, maintaining access allows hackers to stay in the system until all the valuable data has been gathered and extracted. Ethical hackers can install backdoors, rootkits, or Trojan horses for continued access, even if the device receives reboots or patches. Tools such as Netcat, Ngrok, and Empire can be used to maintain access. The standard methods to maintain access are:
- Installing backdoors
- Creating hidden user accounts
- Tunneling
- Keystroke Logging
- Trojan Horses
Covering Tracks
A good ethical hacker doesn’t leave evidence. The last phase involves taking skillful measures to eliminate evidence or proof of any attack. This includes deleting logs, hiding files, and manipulating timestamps. Hackers usually accomplish this by uninstalling all the apps used to gain access using tools such as CCleaner, Stealth Rootkit, and Timestomp. The common methods to clear and cover tracks in ethical hacking are:
- Log Tampering
- Steganography
- File Timestamp Alteration
- Clearing Command Histories
- Encryption
Once the five steps are complete, ethical hackers document their findings and offer recommendations to secure the system. This can be followed by penetration testing through a simulated cyberattack, during which ethical hackers can recheck and test the system’s upgraded security.
What Are The Skills Required to Become an Ethical Hacker?
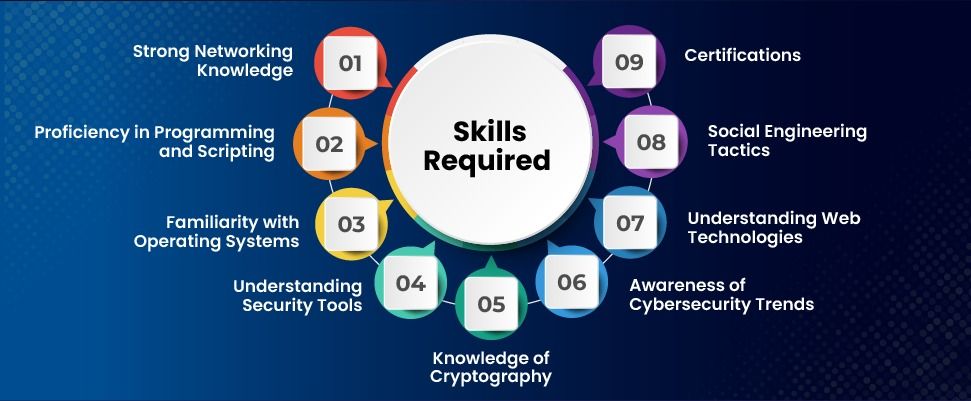
Strong Networking Knowledge
Understanding network protocols, IP addressing, subnetting, firewalls, VPNs, and network security devices is crucial for identifying and exploiting network vulnerabilities.
Proficiency in Programming and Scripting
Knowledge of programming languages like Python, Java, and C++, as well as scripting languages like Bash or PowerShell, is essential for writing exploits, automating tasks, and understanding software vulnerabilities.
Familiarity with Operating Systems
Expertise in various operating systems, particularly Linux, Windows, and macOS, is necessary for navigating and exploiting these environments.
Understanding Security Tools
Proficiency in using security tools such as Nmap, Metasploit, Wireshark, Burp Suite, and Nessus for scanning, penetration testing, and vulnerability assessment.
Knowledge of Cryptography
Understanding cryptographic techniques and algorithms, and how they can be used or broken, is vital for securing data and identifying weaknesses in encryption protocols.
Awareness of Cybersecurity Trends
Staying updated with the latest threats, attack techniques, and security technologies is crucial for effective ethical hacking.
Understanding Web Technologies
Knowledge of web development, HTML, JavaScript, and SQL is essential for identifying and exploiting web application vulnerabilities like SQL injection and XSS.
Social Engineering Tactics
Familiarity with social engineering techniques to understand how attackers exploit human psychology to gain unauthorized access.
Certifications
Earning certifications such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), or Certified Information Systems Security Professional (CISSP) can validate and enhance your skills in the field.
What Are the Benefits of Ethical Hacking?
- Identify Security Flaws
It helps uncover vulnerabilities in systems, applications, and networks, allowing organizations to address them before they can be exploited.
- Enhance Security Posture
Regular assessments enable organizations to strengthen their security by fixing identified weaknesses and implementing best practices.
- Prevent Data Breaches
By proactively testing security measures, ethical hacking reduces the risk of unauthorized access to sensitive information.
- Build Trust and Reputation
Prioritizing security through ethical hacking enhances an organization’s reputation and builds trust with customers by showing a commitment to safeguarding information.
- Raise Awareness
It provides valuable insights into potential attack vectors, helping organizations train employees and increase awareness about security risks.
- Ensure Compliance
Ethical hacking helps organizations meet regulatory and industry standards like GDPR, HIPAA, and PCI-DSS, demonstrating a commitment to data protection.
- Cost Savings
Early identification and remediation of vulnerabilities can save organizations significant costs associated with data breaches, legal liabilities, and reputation damage.
- Proactive Risk Management
Ethical hacking allows organizations to identify and mitigate potential threats before they become critical issues.
- Improve Incident Response
By simulating real-world attacks, ethical hacking helps organizations test and improve their incident response plans.
- Support Innovation
Ensuring the security of new products and services through ethical hacking helps organizations confidently launch new initiatives.
Also read: How to Start a Career In Cybersecurity Types of Ethical Hacking

System Hacking
Ethical hackers get into individual systems to carry out malicious actions, gain unauthorized access, or escalate privileges. System hacking requires ethical hackers to be good at cracking passwords, exploiting vulnerable systems, and installing malicious software.
Example: Suppose a company hires a penetration tester to evaluate the security of a company’s internal systems.
The tester carries out an assessment, finds the vulnerability, and gains administrative access to the system. Then, they show the company how an attacker could use the same access to install malicious software, steal sensitive data, or disrupt operations. The tester then recommends patching the vulnerability and improving overall system security.
Network Hacking
Ethical hackers hired for network hacking work on detecting weaknesses in network security. They scan the network for open ports, identify vulnerable services, and exploit network protocol weaknesses. They then gain unauthorized access or disrupt services.
Example: A financial institution can hire a team of ethical hackers to conduct penetration testing on its internal network. By using network scanning tools, ethical hackers can identify open ports and services, outdated versions of network services, and more. They then exploit this vulnerability to gain unauthorized access to the network and demonstrate how an attacker can access sensitive financial data and potentially disrupt critical services. The detailed report and recommendations from the team help the financial institution implement stronger network security measures.
Web Application Hacking
Ethical hackers take advantage of security loopholes in web application security systems to gain unauthorized access. They then change data and perform malicious actions.
Example: A penetration tester can use methods like SQL injection or XSS to inject malicious code or scripts into a web application to show the app owner how it can be hacked. Based on the recommendations, the app can be improved and made more secure.
Wireless Network Hacking
Wireless networks are generally more prone to hacks, as they broadcast data all over the air, making it easy for hackers to intercept and capture data packets without physical access. Ethical hackers gain unauthorized access to the wireless network or intercept data, demonstrating how strong or weak a wireless network is in terms of security.
Example: Wireless network companies hire ethical hackers to test the security of their networks, identify vulnerabilities, and fix them. Hackers can use wire cracking, packet sniffling, and other methods to discover and address vulnerabilities and ensure that wireless networks are protected against unauthorized access and data breaches.
Ethical Hacking of Mobile Platforms
This involves hiring ethical hackers to find loopholes in mobile operating systems (Android, iOS) and applications. This helps discover unsafe data storage, poor transport layer protection, and ineffective authentication mechanisms.
Example: A security team is hired to evaluate a new mobile banking app. It discovers that the app stores sensitive user data in plaintext on the device, posing a risk if the device is lost or stolen. To enhance security, they recommend encrypting the data.
Social Engineering
Ethical hackers manipulate human psychology and pretend to be a trustworthy entity. They then lure users into revealing sensitive information or performing actions that compromise security by pretending to be trustworthy. Social engineering helps evaluate employee awareness and response to phishing attacks.
Example: Ethical hackers are hired by companies to see how familiar employees are with digital scams. They could leave an infected USB in common areas or call employees pretending to be from the IT department.
Reverse Engineering
It involves the process of hiring security researchers to take a piece of malware and go back, that is, reverse engineer the malware to understand how it infects systems and to develop countermeasures.
Example: Reverse engineers can work on old software to develop a compatible interface for modern applications, ensuring functionality and seamless exchange of data.
Physical Hacking
Ethical hackers get unauthorized physical access by installing devices to capture keystrokes or other data. Physical hacking helps identify the security of physical entry points, such as doors, locks, and biometric systems.
Example: An ethical hacker can use hardware keyloggers on a public computer to capture users’ login credentials. This can be used to check if sensitive information is being leaked and if appropriate measures can be taken.
Cloud Security Testing
Ethical hackers simulate cyberattacks on cloud infrastructure to identify and fix security weaknesses through penetration testing. This helps determine the security of a company’s cloud service.
Example: Hackers can exploit misconfigured settings, weak passwords, or unpatched vulnerabilities in cloud services through simulated attacks. This helps cloud service providers maintain robust security.
IoT (Internet of Things) Hacking
Ethical hacking for IoT devices involves getting unauthorized access or control to explore the vulnerabilities of IoT devices. IoT ethical hacking ensures the security and integrity of IoT devices and systems.
Example: Ethical hackers can test smart home devices to find vulnerabilities and ensure that personal data is not exposed.
Different Types of Hackers
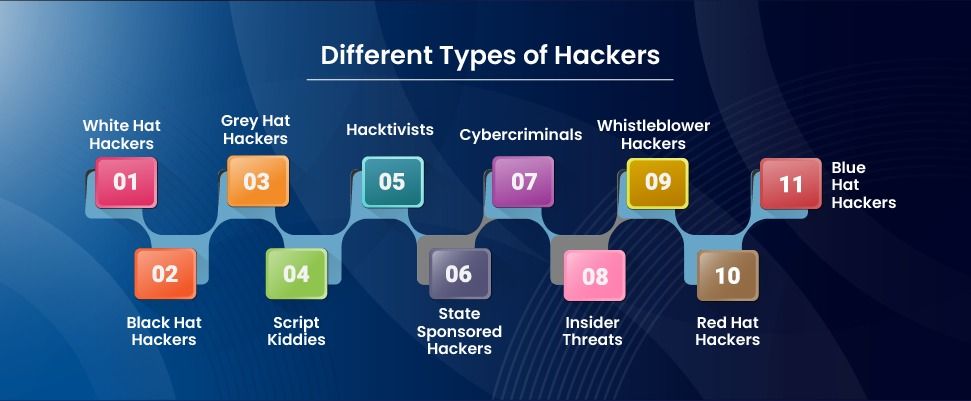
White Hat Hackers
Ethical hackers who identify and fix security vulnerabilities for organizations are referred to as white hat hackers. They work with permission and adhere to legal guidelines.
Black Hat Hackers
They are malicious hackers who exploit vulnerabilities for personal gain. Black hat hackers operate illegally and intentionally cause harm to individuals, organizations, or systems.
Grey Hat Hackers
These are hackers who fall between white and black hats. They may exploit vulnerabilities without permission, but it is not for any malicious intent. The flaws publicly or to the organization afterwards.
Script Kiddies
Inexperienced hackers using pre-written scripts or tools to carry out attacks are referred to as Script Kiddies. They don’t have a deep understanding of the underlying technology of systems and network services.
Hacktivists
Hackers who carry out hacking activities to promote political or social causes are called hacktivists. They are known to deface websites or release sensitive information to support their agenda.
State-Sponsored Hackers
These are hackers usually employed or sponsored by governments They work for government secret agencies and conduct cyber warfare, or surveillance activities against other nations, organizations, or individuals.
Cybercriminals
Hackers engaging in illegal activities for financial gain are referred to as cybercriminals. They are infamous for stealing credit card information, conducting ransomware attacks, or running phishing scams.
Insider Threats
Hackers who misuse their access within their organization are called insider threats. They can act intentionally or unintentionally for malicious purposes or personal gain.
Whistleblower Hackers
Individuals exposing unethical or illegal activities within organizations are whistle blower hackers. They hack into systems and leak sensitive information to the public or authorities.
Red Hat Hackers
These are vigilante hackers targeting black hat hackers and cybercriminals. They use aggressive methods to shut down malicious operations.
Blue Hat Hackers
They are security professionals invited by organizations to test their systems. They are experts who are hired externally and are not employed by the organization.
Where Can One Learn Ethical Hacking?
Various online platforms like Coursera, Udemy, and TryHackMe offer courses on ethical hacking. These platforms offer comprehensive courses covering cybersecurity fundamentals, penetration testing, and advanced hacking techniques. Additionally, websites like FreeCodeCamp and Edureka provide free resources and tutorials to help you get started. Platforms like Hack The Box and TryHackMe also have interactive labs and challenges for hands-on practice. Here are a few relevant ethical hacking certifications:
CompTIA PenTest+: An entry-level certification that covers essential penetration testing and vulnerability assessment skills. CompTIA has four IT certification series that test different knowledge standards – from entry-level to expert.
Certified Ethical Hacker (CEH): Offered by the EC-Council, this certification focuses on understanding and using hacking tools and techniques to identify vulnerabilities.
Offensive Security Certified Professional (OSCP): Known for its rigorous hands-on approach, this certification emphasizes practical penetration testing skills
GIAC Penetration Tester (GPEN): This certification covers advanced penetration testing methodologies and techniques.
IBM Cybersecurity Analyst: This certification equips you with the skills needed for a career in cybersecurity.
Certified Information Systems Security Professional (CISSP): While broader in scope, this certification includes significant content on ethical hacking and security management.
Ethical Hackers' Code of Ethics
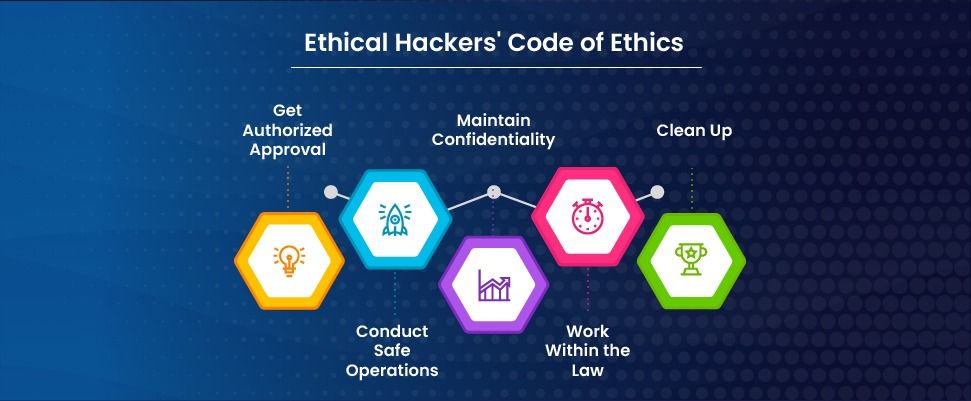
Ethical hackers must adhere to specific guidelines to conduct hacking activities legally. A proficient ethical hacker understands their responsibilities and follows all ethical standards. Here are the key principles of ethical hacking:
Get Authorized Approval
Ethical hackers should obtain explicit permission from the system’s owner before conducting any security assessment on the system or network. They should work with the organization with a clearly defined scope of work and timelines.
Conduct Safe Operations
Ethical hacking is supposed to only demonstrate the harm that hackers can cause to systems. Hence, ethical hackers should not cause any harm to the systems, steal information, or misuse sensitive data.
Maintain Confidentiality
Ethical hackers must keep all the findings confidential. There is a non-disclosure agreement between the hacker and the client which must be honored at all times.
Work Within the Law
Ethical hacking should only involve legal methods for information security. Any activity done bypassing legal methods makes ethical hackers slide into the category of black hats.
Clean Up
As mentioned earlier, a good hacker never leaves any trace. Ethical hackers must remove all traces of the hack after identifying vulnerabilities. This ensures that hackers can’t exploit the same weaknesses to launch malicious attacks or exploit sensitive information.
Conclusion
Ethical hacking, while beneficial for identifying and reducing security vulnerabilities, does have several limitations. Ethical hackers must do their work within a predefined scope, which can limit their ability to uncover all potential vulnerabilities. Additionally, they often face time and budget limitations along with resource constraints, which can limit the depth and breadth of their testing. Moreover, ethical hackers also face a lot of legal restrictions, which might force them to use limited methods for their assessments. However, ethical hacking remains a crucial component of a comprehensive cybersecurity strategy despite these limitations. It helps organizations proactively identify and address vulnerabilities before malicious hackers can exploit them. Sign up with Olibr now to find the best job opportunities.
Take control of your career and land your dream job
sign up with us now and start applying for the best opportunities!


